
This are the functions for registration and login:
- Registration
- Activation
- Login, Logout, Send password
- Account data
- Admin user list
- Login control
- Auto login by cookie
- Auto logout
- Ini Parameter
- Data access rights
- Backend
- Customizing
Registration
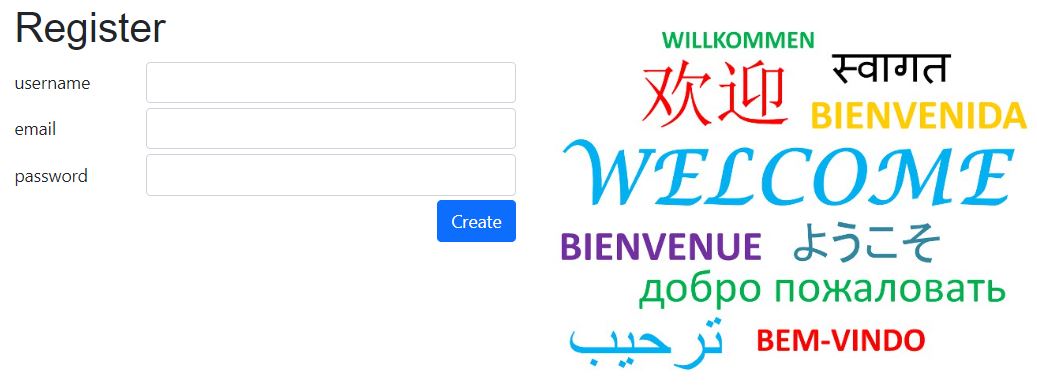
Password configuration
The password configuration is defined in config/_init.php:
- config:
- passwordrule: "^.{6,12}$" (Regex Tester)
- passwordhint: "6-12 caracters"
- expiration_activation: 144 (hours)
- expiration_pwdreset: 60 (minutes)
Registrations, which are not activated before the expiration will be deleted (executed in the activation function).
Resources:
- page=register (js/example.js)
- datadefID=k8loginregister
- config/_init.php
- domain_registermode
- 0: only username+email
- 1: with address
- 2: register username+email,
my data with address
- domain_registermode
Functions:
- username: unique
- email: unique,
but testmail not unique for testing - password (minlength=6)
To do changes, copy the datadefinition folder "k8loginregister" from "masterdata" to your project folder.
The default roles can be changed in masterdata/k8login/k8login.json:
- columns
- Field: "roles"
- mydefault: "3,5,30"
- Field: "roles"
Activation
The activation (page=activate) is placed in the index.php file.
Login, Logout, Reset password
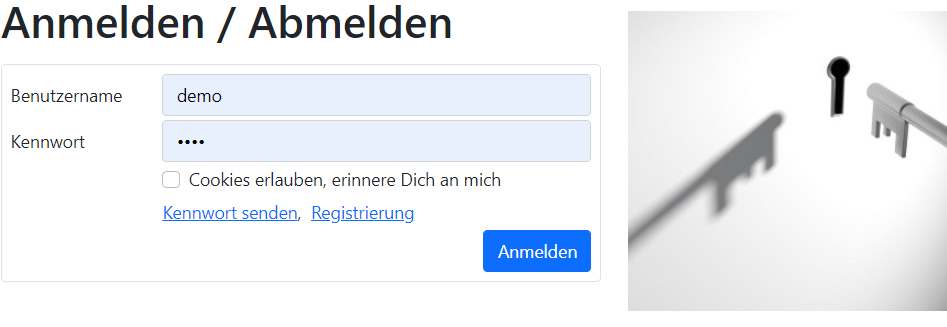
page=login (index.php)
Functions:
- Login
- Logout
- Reset password
Account data
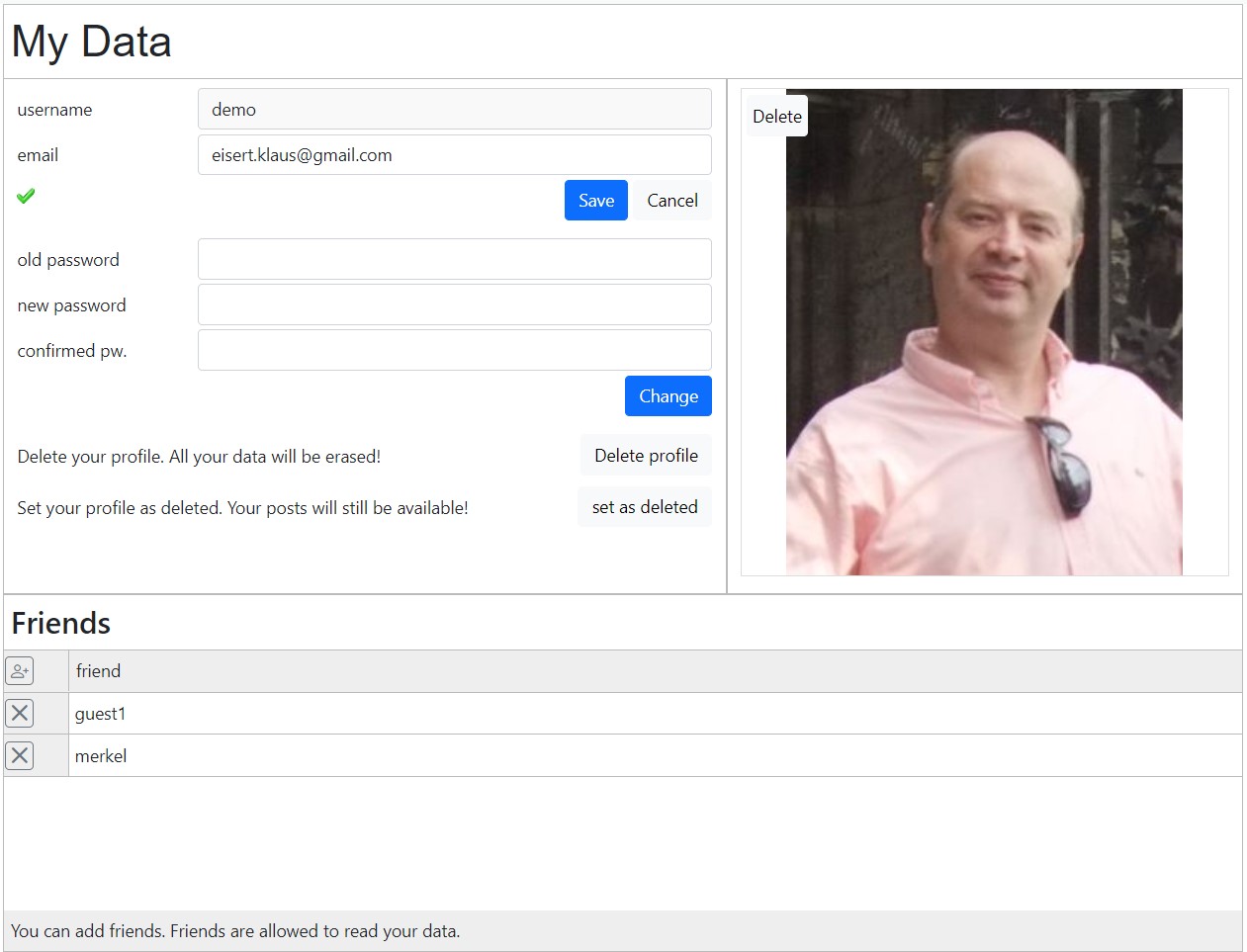
Resources:
- page=mydata (example.js)
- datadefID=k8login
Adopte the appearance of the page with the following parameter in the datadefinition, masterdata/k8login.json:
To disable it all, set it to false:
- upload
- enabled : false
- showdelete : false
- showsetdelete : false
- addfriends : false
Admin user list
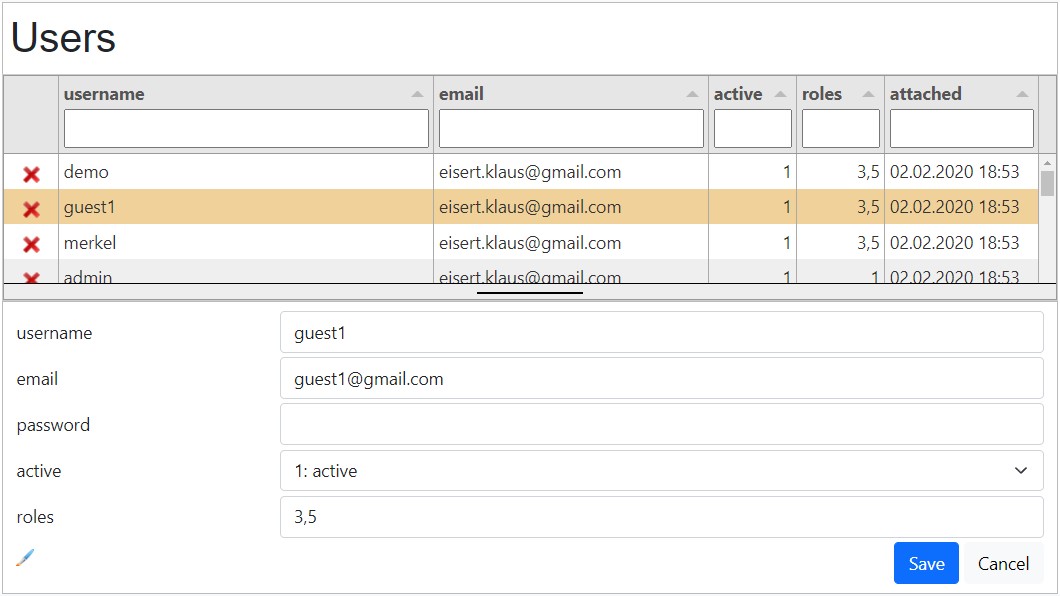
Resources:
- page=user_list (example.js)
- datadefID=k8login
As admin you have the following functions:
- edit user
- delete user
Login control by page
Query Parameter, for example: page=item_list
For the page "item_list" a logged in user is necessary. _init_page.php, $pages['item_list']:
- login=true
In _init_page.php the login status is checked. If the user is not logged in, the login page is displayed first. By succesful login the required page "user_list" is displayed.
The login control checks:
- page needs login? Yes
- user is logged in? No
-> Login page is displayed first!
Auto login by cookie
- index.php
- masterdata/ProcessData.php
- masterdata/ProcessMethods.php
If the user hooks "remeber me" by login a cookie is set. The following files check the cookie, when the userID is 0 and execute an login:
Thanks to the auto login by cookie you are logged in even you are clicking the save buttons after hours of absence.
Auto logout
If no cookie is set the auto logout is active. Each Ajax call resets the timer. The timer "var pagetimer" is set in js/example.js to 20min.
By absence or inactivity your are logged out automtically (default: 20min).
Configuration in init.php
| Parameter | Description |
|---|---|
| domain_registerenabled | 0 : registration is disabled 1 : registration is enabled 3 : registration still in menu, but not yet available |
| domain_registermode | 0 : only username and email 1 : username, email and address 2: register username+email, my data with address |
| domain_useractive |
0 : direct after registration 1 : with activation mail |
| domain_activekey | 1234 : with this factor the activation key is encoded, please put your own number in. |
| domain_readpassword |
0 : off, the password is never read 1 : password read by user and admin 2 : password read only by user 3 : password read only by admin 4 : only password hash is saved, Attention: after installation both values are in the database, change the passwords for this rule! |
| domain_loginenabled | 0 : login is disabled 1 : login is enabled |
| domain_roles | 1 : admin, all rigths for client 2 : superuser, all rights in database 3 : member, logged in user 5 : friends, added in my data 30: right groups, look social groups below |
| domain_rightmode | 0 : Standard 1 : with clients 2 : with right groups |
| domain_testemail | empty or example: user@yourdomain.com Normally an email has to be unique in your application. For your own testing this email is an exeption. |
| domain_email | If you use only your native language write please your own text here. If you use multiple languages, change it please in the masterdata/js/lang_sys_<language>.js file. |
| ['activate']['subject'] | activate your account |
| ['activate']['content'] | Dear member, please activate your account: <a href="{{activation_link}}">activation link</a> Greetings {{domain_name}} |
| ['resetPwd']['subject'] | reset password |
| ['resetPwd']['content'] | Dear member, you ask to reset your password: <a href=\"{{reset_link}}">reset link</a> Greetings {{domain_name}} |
Please edit the file config/_init.php.
Data access rights with RBAC
RBAC (Role Based Access Control) assigns the user to 1 or more roles. Roles restrict or authorize the access to tables and records. This rights can only be granted by using the login with php sessions. The RBAC is implemented in the PHP data access class. The access check is activated for an object in the datadefinition by setting "rightcheck=1". In the data table the column "creatorID" is added. Comparing the creatorID with the logged in user gives the result: own record or foreign record.
By opening the website the user is assigned to the role "0:public". His userID is also 0. By login the role is replaced by the default roles of the login table: k8login.roles="3,5". The userID is set. For each object or table, for each CRUD operation (create, read, update, delete) and role an access check is implemented.
This is the data access definition in the datadefinition (masterdata.rights):
- CRUD Operation
- Role-ID
- Method for access check
- Role-ID
Thanks to the roles and data access methods, you can easyly grant the rights of your CRUD operations.
RBAC with K8 Web Kit
Roles
$GLOBALS[domain_roles]:
- roleID:
- name
Users and role membership
table k8login:
- userID
- roles (roleID-1, roleID-2)
comma separated roleIDs
Datadefinition / table
- CRUD Operation
- Role-ID
- Method for access check
- Role-ID
Methods
- 0: not granted
- 1: table.clientID=SESSION[clientID]
- 2: granted
- ...
- 10: table.creatorID=SESSION[userID]
Roles
The roles are defined in:
- config/_init.php
Users and role membership
The initial roles are the default value in the columns array of the datadefinition "k8login". It can be changed in the user list by super user or admin.
Datadefinition / table
In the datadefinition the rights are written in:
- masterdata
- rights
Methods
The methods are checked before or by executing the sql statement.
| Operation | SQL command | data access function |
|---|---|---|
| Create | INSERT | add() |
| Read | SELECT | getEntries() |
| Update | UPDATE | update() |
| Delete | DELETE | delete() |
By each CRUD operation the data access is checked in the correspondent data access function.
| ID | Role | Comment |
|---|---|---|
| 0 | public | user not logged in |
| 1 | admin | all rights in a client |
| 2 | superuser | all rights in the database |
| 3 | member | logged in user |
| 4 | employee | logged in user |
| 5 | friend | assigned in table: k8loginfriends |
| 6 | company, own data | domain_rightmode=3 |
| 7 | company, admin | domain_rightmode=3 |
| 19 | company login | domain_rightmode=3 |
| 21 | company read | domain_rightmode=3 |
| 25 | company create standard | domain_rightmode=3 |
| 30 | rightgroups | assigned in tables: k8rightgroups, k8rightmembers |
| x | others | create by yourself |
config/_init.php, domain_roles:
The available roles are defined in the "../config/_init.php".
Roles by login:
Each user can get assigned to 1 or several roles. The default roles can be set in masterdata/k8login/k8login.json, property: columns / roles / mydefault in a comma separated string like "3,5".
Admin / user list:
Superuser or admin can change the user roles in the user_list.
| Number | Check method |
|---|---|
| 0 | no rights |
| 1 | access permission in this client: table.clientID=$_SESSION[clientID] |
| 2 | permission granted |
| 3 | user logged in: $_SESSION[userID]<>0 |
| 4 | table.companyID=$_SESSION[companyID] |
| 5 | table.creatorID=$_SESSION[userID] table.companyID=$_SESSION[companyID] |
| 10 | table.creatorID=$_SESSION[userID] |
| 11 | check friend k8loginfriends.friendID=$_SESSION[userID] |
| 13 | checks membership in right groups |
| 14 | checks the rights of the active right group (rightgroupID) of the user: create: k8rightmembers.rightgroupID=$_SESSION[rightgroupID] and k8rightmembers.userID=$_SESSION[userID] and status>1 read: $table.rightgroupID=$_SESSION[rightgroupID] and k8rightmember.userID=$_SESSION[userID] and status>0 update: $table.rightgroupID=$_SESSION[rightgroupID] and k8rightmember.userID=$userID and ((k8rightmembers.status=2 and $table.creatorId=$userID) or k8rightmembers.status=3)) delete: same update |
| 1000 | check parent table access rights |
| ... | programm your own check |
By each CRUD operation the access rights are checked. If the operation by Create, Update or Delete is not granted, an error is returned. Reading a table can return an empty recordset, because of the missing rights.
By Read the results of the access check for Update and Delete are returned in advance like this:
- in the datadefinitition:
- masterdata.rightuser_create: true
- by reading the recordset:
- rightuser_update: true
- rightuser_delete: true
To check the user right by foreign tables the table can be joined or checked by "EXISTS()":
Access methods can depend:
- on a column of your own table
- or depend on a column of a joined table
This are the default rights (config/_init.php):
| Roles | ||||
|---|---|---|---|---|
| Operation | 0: public | 1: admin | 2: superuser | 3: member |
| Create | 0 | 1 | 2 | 2 |
| Read | 2 | 1 | 2 | 2 |
| Update | 0 | 1 | 2 | 10 |
| Delete | 0 | 1 | 2 | 10 |
table cell = access method:
- =0: denied
- >0: granted by the method
The default rights are declared in the _init.php. They can be overwritten in the datadefinition.
datadefinition:
- masterdata
- defaultrights=true (default)
- rights
- create
- "0":2
- ...
- ...
- create
masterdata/_init.json
This are the default rights of the initialization.
Rights from the datadefinition overwrite the default rights. To allow the roles, public and member, to read all records in the object, add in the datadefinition:
The following rights are changed:
- create:
- 0: public
- 2: granted, can register and add a record
- 0: public
- read:
- role "0" public is not allowed to read the data
- update / delete:
- same, like default
Rights from the datadefinition overwrite the default rights. To allow the roles, public and member, to read all records in the object, add in the datadefinition:
Rights from the datadefinition overwrite the default rights. To allow the roles, public and member, to read all records in the object, add in the datadefinition:
| Roles | |||||
|---|---|---|---|---|---|
| Operation | 0: public | 1: admin | 2: superuser | 3: member | 4: employee |
| Create | 0 | 1 | 2 | 0 | 2 |
| Read | 0 | 1 | 2 | 0 | 2 |
| Update | 0 | 1 | 2 | 0 | 10 |
| Delete | 0 | 1 | 2 | 0 | 10 |
table cell = access method:
- =0: denied
- >0: granted by the method
The default rights are declared in the _init.php. They can be overwritten in the datadefinition.
Attention:
The rigths for public tables, for example: "k8pages", need to be changed!
Rights from the datadefinition overwrite the default rights. To allow the roles, public and member, to read all records in the object, add in the datadefinition:
This are the default rights for a scret company in json!
The access right of the table depend on another master table. In this case the master table needs to be checked for the access rights. This is declared in the datadefinition:
Link to master
The masterdatadefID declares the master datadefinition. The first right check is made by this datadefinition. The masterkey defines the colun of this table, which correspond to the master key column of the master datadefinition.
Access right: read
- first the acces rights of the master is checked
- The right of the master is heritated to the child by the method: 1000
Access rights: create, update, delete
- first the right "Update" of the master is checked
- The right of the master is heritated to the child by the method: 1000
In this example the the access for role 2 is granted to all CRUD methods. The role 3 herites the access from the master.
Using clients
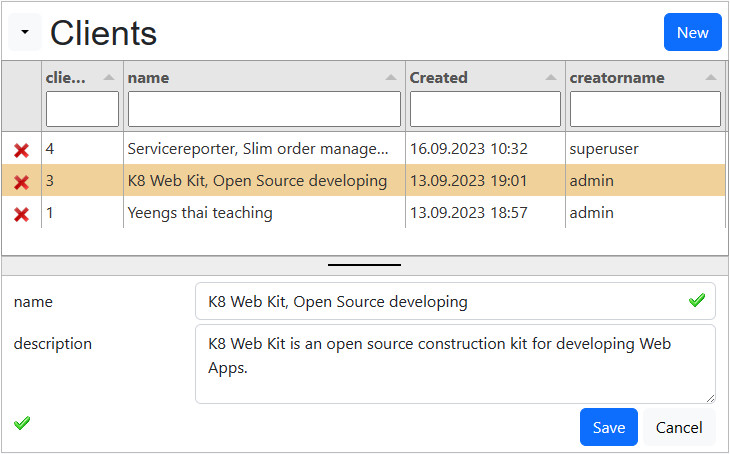
Allow multiple clients to use your Web App. Each table has a clientID to differentiate the data from each other. Each Client has an own admin to govern his data and user. The user registers for 1 client. For each client he needs a different email.
Preparation
config/_init.php:
The domain_rightmode==1 enables:
- register: selection of the client
- menu Admin: display "Clients"
Social groups (right groups)
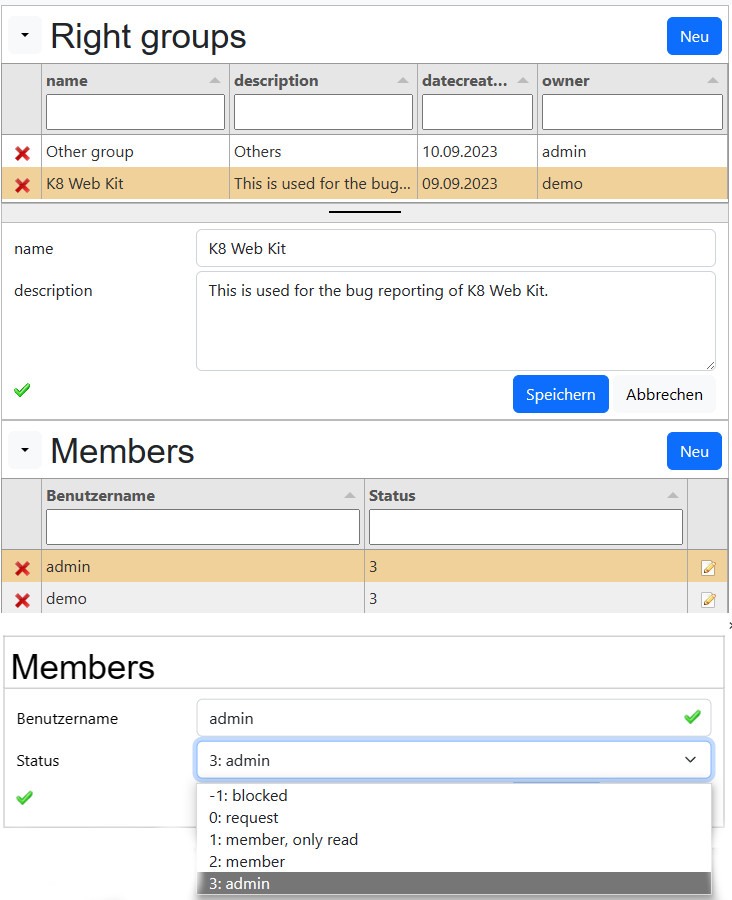
Social groups are part of many social platforms like facebook and others. Properties of a social group are:
- Title
- Description
- Owner
- Picture
- Members
- Admins
- Observers
- Members
This are the involved datadefinitions:
- k8rightgroups: the group header (folder: masterdata)
- k8rightmembers: the group members (folder: masterdata)
- your table: for example the postings
The rights of the member are defined in the column "status" in "k8rightmembers".
The data access methods are:
- 13: all records with group membership
- 14: filtered to rightgroupID in SESSION
Create a group
- Users with the role 30 have the right to create a right group
- the creator is added as admin
Frontend
- User
- Listing of his groups: membership
- Right group catalog
- Right group form
- Member list (request)
- Admin
- Masterdata form with all groups
13, right group is added by the form
Attention:
- rightgroupID needs to be a field in the form!
This is the "right" definition of the masterdata section:
14, filtered to rightgroup in SESSION
Attention:
- right group has to be choosen in My data (SESSION variable)!
This is the "right" definition of the masterdata section:
By writing a new record the rightgroup is filled automatically with the SESSION rightgroupID.
Your datadefinition
Your table need to contain the column:
- rightgroupID(INT), attention no update
You need to define special rights:
- look above, rights for method 13 or 14
The Menu
The following variables are available in JavaScript:
- dat_user.roles: create a special role for your rightgroups
- rightgroupID: the SESSION[rightgroupID]
- GLOBALS_config['rightidentifiers']: array with all identifiers of the rightgroups with membership.
Preparation (14)
config/_init.php:
The domain_rightmode=2 enables:
- my data: selection of the right group
- data access class:
- validation: check the right group
- add: adds the rightgroupID from SESSION variable
Example for right groups (13): Bug Reports

Elements of Bug Reports:
- Projects
- table: k8projects
- datadefID: projects
- Bug Reports
- table: k8bugs
- datadefID: bugreports
- Bug Fixes
- table: k8bugfixes
- datadefID: bugfixes
Data access:
- Roles:
- 101: Bug fixes
- rightgroups:
- identifier: Bug Reports
Right groups in master data form (13)
The project in the head is assigned to a rightgroup. Without project no new records are allowed. After selecting the rightgroup the rights are checked. The records are displayed. If the create right is granted, a new record can be added.
Example for projects (13)
extract of project datadefinition:
The following rescources are added:
main
- JavaSript file: projects_head_end.js
- datadefinitions: k8rightgroups
masterdata
- the rights are defined
- the SQL statement is expanded with rightgroupname
tabulator
- the rightgroupname is added to the columns
k8form
- the form element rightgroupname is added as datalist
JavaScript:
The following configurations are made:
- GLOBALS_rightmode==2 (14)
- rightgroupname is not displayed
- GLOBALS_rightmode!=2 (13)
- Button "New" is activated
Company with employees

Allow companies to create an account and to add employees:
Own data access methods
| Operation | Function | Return values |
|---|---|---|
| Create | bRecordAccess() | true / false |
| Read | bRecordReadPermission() |
$out[]:
|
| bRecordUDPermission() |
$out[]:
| |
| Update | bRecordAccess() | true / false |
| Delete | bRecordAccess() | true / false |
bRecordReadPermission()
This function creates a clause which which determines which records are read.
bRecordUDPermission()
This function is called 2 times and creates the columns for the data access "update" and "delete":
- rightuser_update: 0/1
- rightuser_delete: 0/1
In config/_init.php the variable $GLOBALS['domain_includes'] allows to include own PHP files to write your own methods:
- [RBAC_Read]:bRecordReadPermission()
- [RBAC_RUD]: bRecordUDPermission()
- [RBAC_CUD]: bRecordAccess()
Backend
The data access in the backend is controlled by PHP with $_COOKIE and $_SESSION.
$_COOKIE
- login
$_SESSION
- userID
- username
- password
- roles[]
- dat_user[]
table: k8login
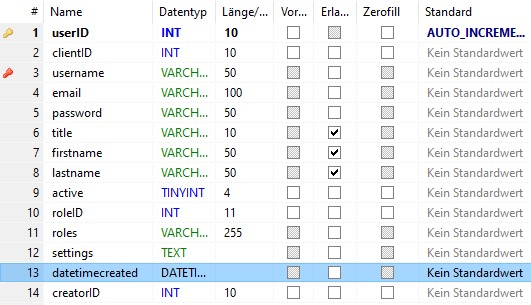
active
- 0 : registrated
- 1 : active
- 2 : blocked
- 3 : deleted
datadefinition=k8login, masterdata/k8login/k8login.json
Resources:
- $_COOKIE
- $_SESSION
- table: k8login
- datadefinition: 5
- k8login.json
Customizing
In the datadefinition under masterdata the include files are defined:
If you are changing it, copy it to your project folder and adopt the path.
k8login_validate.phpAdopte the validation to your needs.
k8login_afterinsert.phpHere you can prepare records for the new members.
k8login_beforedelete.phpIf you have to delete records of this member, please do it here.
| Parameter | Description |
|---|---|
| domain_includes[] | To extend the basic functionality, please use this include files: |
| ['login'][] | array("kitsamples/_kitsamples_login.php"); In the referenced php file you can enter your lines to extend your login. |
| ['logout'][] | array("kitsamples/_kitsamples_logout.php"); In the referenced php file you can enter your lines to extend your login. |
Resources:
- masterdata/k8login.json, masterdata.includes:
- k8login_validate.php
- k8login_afterinsert.php
- k8login_beforedelete.php
- config/_init.php, domain_includes
- login
- logout